
How I Organized a CTF for a Junior-Enterprise Congress
Organizing a Capture The Flag (CTF) within the framework of a student congress is an excellent way to raise awareness about cybersecurity , OSINT , and personal data protection , while offering a fun and collaborative activity. In this article, I share my experience organizing my first CTF, set up during a Junior-Enterprise regional congress.

Event Overview
During my mandate as an IT Manager & DPO at the Junior-Enterprise Polytech Services Nancy, I designed and organized a CTF for the 2024 Autumn Regional Congress (CRA) of the Eastern region of Junior-Enterprises, which focused on “Data in Junior-Enterprises.” The event took place at Polytech Nancy from October 11 to 13, 2024.
In total, 13 different Junior-Enterprises were represented, with approximately 40 participants. These Junior-Enterprises are members of the National Confederation of Junior-Enterprises (CNJE). Due to the diversity of the Junior-Enterprises involved, the audience had varying levels of awareness regarding the topics covered during the event.

Preparing the CTF
For the technical platform, we chose CTFd, an open source solution widely used in the cybersecurity ecosystem. Its main advantage lies in its deployment simplicity thanks to Docker , as well as its ease of use for creating and managing challenges. The CTF was hosted on a dedicated server, prepared in advance to minimize technical risks on the day of the event.
Organizational Constraints
Several constraints heavily influenced the design of the CTF. The gameplay time was limited to a maximum of one hour, which required short challenges. Teams were formed in advance to save time and encourage interaction between different Junior-Entreprises . Each team consisted of four people, with challenges being solved collectively within the teams. In total, ten teams were divided into three separate rooms.
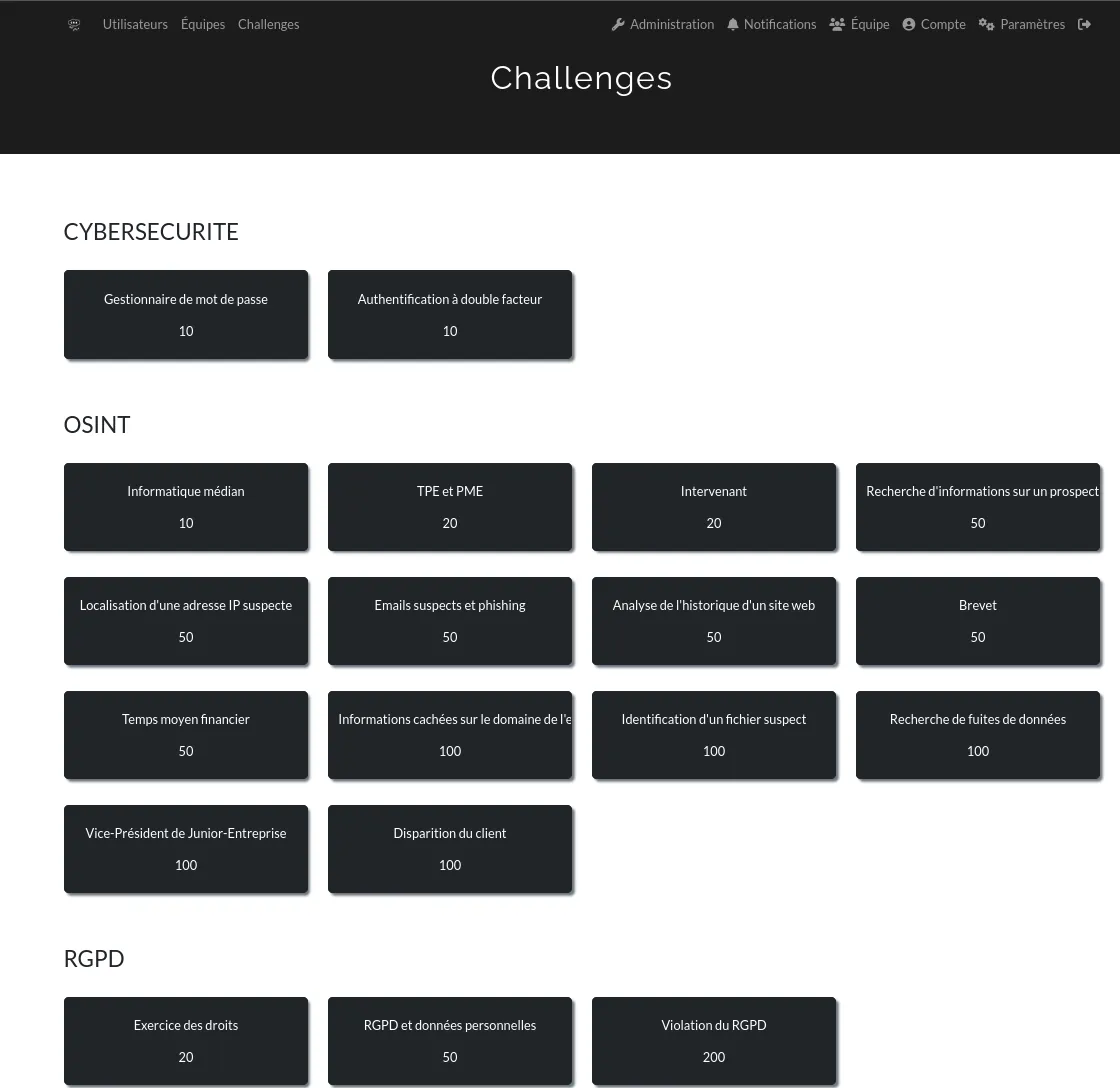
Challenge Themes
A total of 19 challenges were designed. This number seemed appropriate given the time allotted, the assumed level of the participants, and the deliberately progressive difficulty of the tasks.
Open Source INTelligence (OSINT)
Open Source Intelligence (OSINT) refers to the set of techniques used to collect and analyze information from public sources. These practices rely exclusively on legally accessible data, such as social media, websites, or public records.
Although OSINT has historically been used in national security or intelligence fields, it is highly relevant for Junior-Enterprises. It allows them to research potential clients, assess their solvency, or limit the risk of litigation by better understanding their interlocutors.
This theme represented the majority of the CTF, with 14 dedicated challenges.
Cybersecurity
Cybersecurity encompasses all measures implemented to protect computer systems and data against attacks. It concerns individuals as much as companies and student organizations.
Junior-Enterprises handle a significant amount of sensitive data, whether it’s the personal information of their members (ID documents, bank details, social security numbers) or confidential data related to studies conducted for clients. Raising member awareness of these issues is therefore essential to prevent incidents and prepare for cyber-related crisis management.
Two challenges were specifically focused on cybersecurity, drawing notably on the best practices recommended by the National Cybersecurity Agency of France ( ANSSI) , which offers an accessible awareness kit for everyone.
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) is a European regulation that came into effect in 2018, aiming to regulate the processing of personal data within the European Union. It applies to any organization, public or private, regardless of its size or sector.
In France, the CNIL is the authority responsible for ensuring compliance with this regulation. It provides many educational resources, such as The GDPR Workshop, to help learn the basics of the regulation. Three CTF challenges were designed to help participants better understand the legal obligations of Junior-Enterprises.
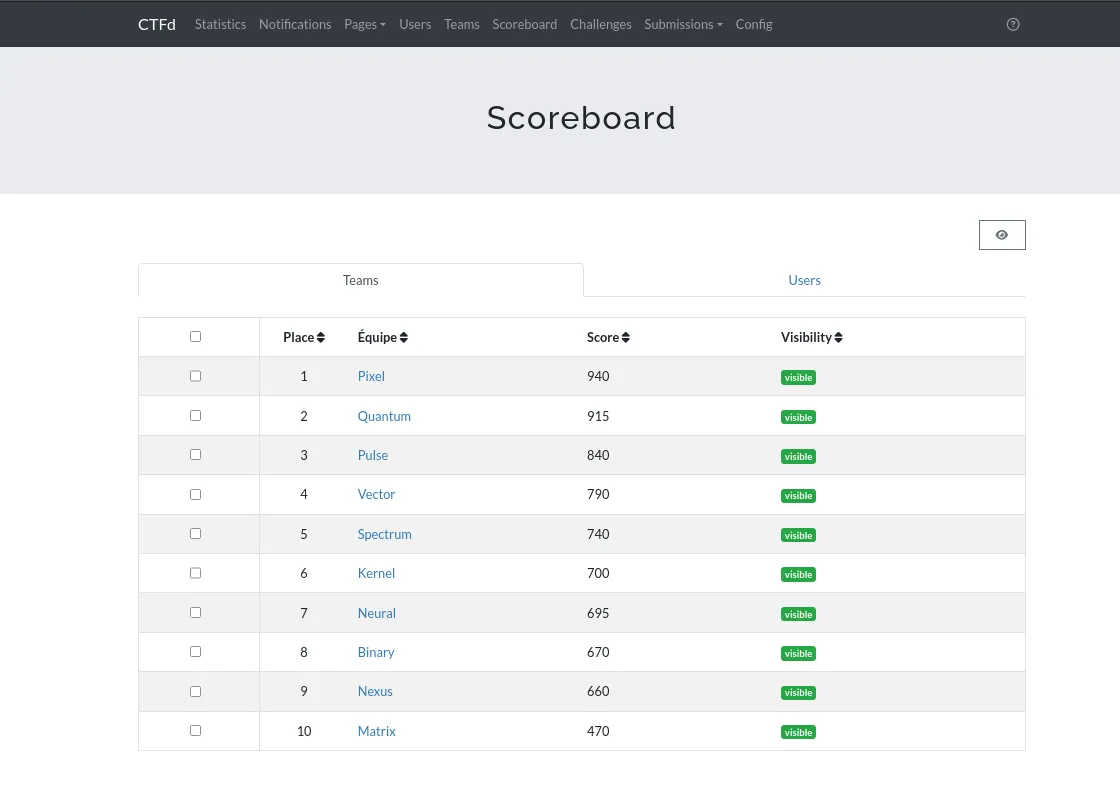
Event Proceedings
Launching the CTF
Before the congress, participants received an email with the terms of participation. This message specified the themes covered, connection details for the CTFd platform, team compositions, room assignments, and an important reminder: bring a laptop.
Unexpected Challenges
As is often the case with technical events, a few surprises occurred. The archive.org (Internet Archive) site was unavailable during the CTF, making it impossible to use the Wayback Machine for certain OSINT challenges. Fortunately, alternative solutions existed, and the participants were able to adapt.
Furthermore, some participants had not brought their laptops. While some tasks could be solved on a smartphone, this wasn’t possible for all challenges. However, teamwork allowed groups to pool their resources and limit the impact of this issue.
Team Organization
Each team adopted a different strategy. Some chose to solve challenges collectively, while others preferred to split tasks based on individual skills. This diversity of approaches enriched the experience and fostered discussions between participants.
Overall, the format was very well received and generated genuine engagement throughout the activity.

Closing and Feedback
At the end of the CTF, participants were thanked for their involvement. A summary document was then sent to them to keep a record of the event, the challenges proposed, and the themes addressed. This document also included additional resources to further explore OSINT, cybersecurity, and GDPR topics.
Organizing this first CTF was an extremely enriching experience that allowed me to fully appreciate the rigor and foresight required for such an event. I would also like to thank all the other members of the congress organizing team for this collaboration: this congress will remain a highlight of my journey as a Junior-Entrepreneur at Polytech Services Nancy.
Finally, it is worth noting that another CTF is regularly organized at Polytech Nancy: the Cyber Humanum Est. This event, led by the Nancy Defense Base and Lorraine INP, is held under the auspices of the Cyber Defence Command (COMCYBER) of the French Ministry of the Armed Forces and the University of Lorraine. It also contributes to raising awareness and training students on current cybersecurity challenges.
To learn more about my journey at Polytech Services Nancy, I invite you to read my dedicated article.
